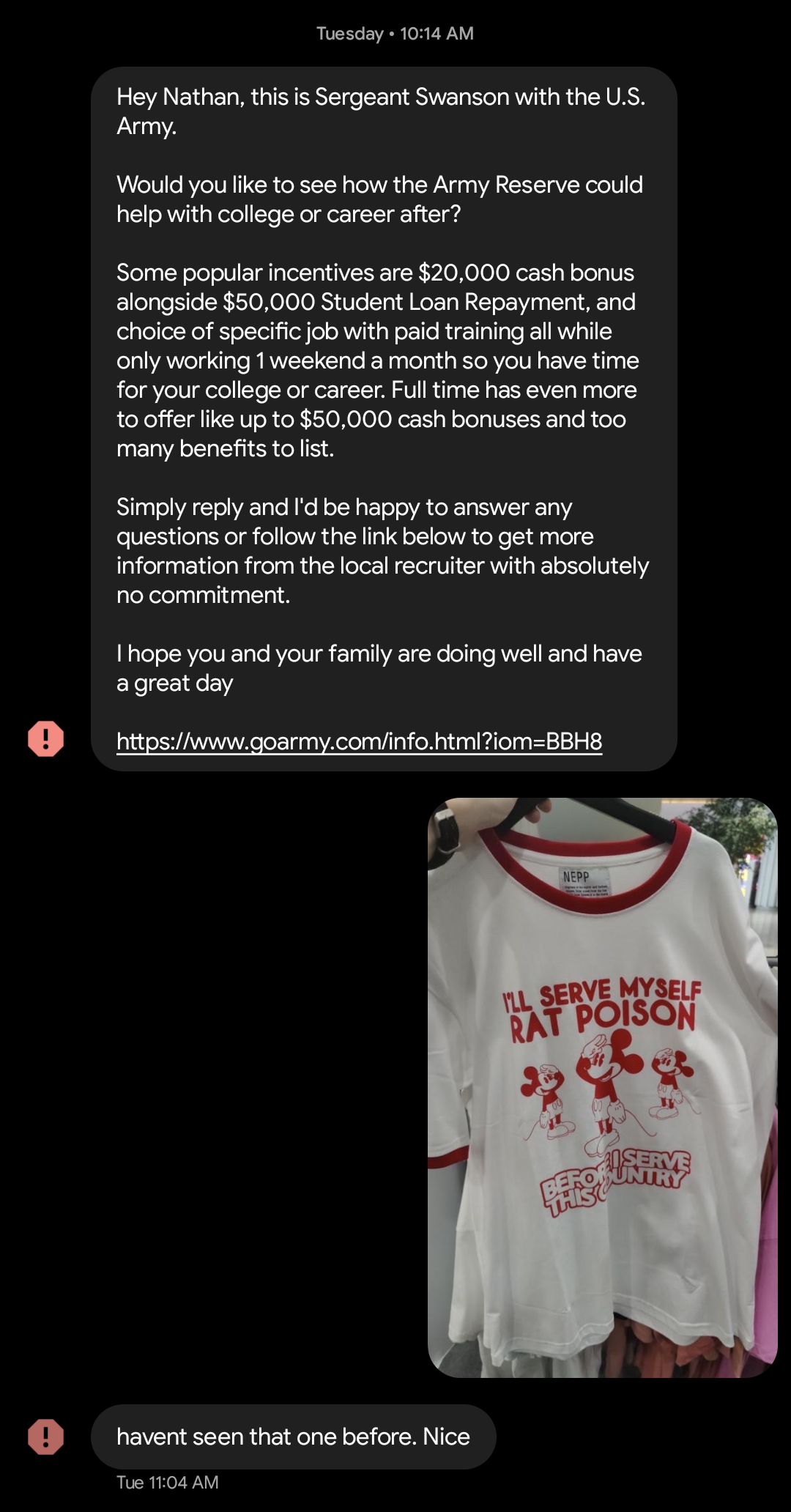
Can confirm they’re real as well as the reaction
- 0 Posts
- 38 Comments
Boomerang was an old feature on Instagram where it would just take a video and then loop it backwards when it reached the end. It was a really stupid phenomenon that nobody really used, hence the reason the got rid of it.
Ctrl + shift + alt + win + any letter opens office apps
- W - Word
- P - PowerPoint
- T - teams
- N - OneNote
…etc
LinkedIn just happens to be L. If there isn’t an app installed (or available) it’ll just open in your browser.
I actually found these a few years ago when I decided to press every modifier letter combination. Back then it wasn’t documented anywhere but I’ve seen it pop up a few times in the last month so somebody must’ve found and shared it recently

 81·2 months ago
81·2 months agoA value is trying to be set on a copy of a slice from a DataFrame. Try using .loc[row_indexer,col_indexer] = value instead See the caveats in the documentation: http://pandas.pydata.org/pandas-docs/stable/indexing.html#indexing-view-versus-copy

 2·2 months ago
2·2 months agoI have a similar thing, it just sends me a notification to my phone on Tuesday night and it won’t let me clear it unless I mark the trash as taken out

 5·2 months ago
5·2 months agoI just moved into a house with my friend and he gave me full reign to smart home the house. Every light has an Innr Zigbee bulb, which are great for having colors during parties and color temperature throughout the day (Adaptive Lighting in HACS), as well as motion controls in the hallway (which has a broken 2 way switch) and kitchen. The front porch light turns on when I come home if I’m on foot, and the back porch light comes on if I’m driving. The lights in the living room turn down if something’s playing and it pauses if I leave the room. We’ve got an old android tablet I stole from the trash on the kitchen wall for a shopping list as well as an overview of the house. They washer and dryer have vibration sensors so we get an alert on our Google homes when our load is finished (we’re both forgetful as fuck). I had an extra contact sensor left over from the doors that I put on the mailbox, so we get a nice AOL “you’ve got mail” when the mailman comes.
Frankly I don’t know how I survived without automation. I forget things so much less now.

 3·3 months ago
3·3 months agoJust took a quick look at my config file and I have
POSTGRES_USER: postgresNote specifically the colon and lack of quotes.
It’s also worth noting I’m using
postgres:16-bullseyeas my image. Something wasn’t working right with latest when I was setting it up a few months ago, but I don’t think it was the user. Regardless, worth a shot if the previous change doesn’t help.

 11·3 months ago
11·3 months ago The secret to it
The secret to it

 5·4 months ago
5·4 months agoIm not sure if it’ll work for your use case, as I don’t have my phone setup like that, but Material Files should be able to do what you’re looking for. I’m able to access my termux directory with Add storage > external storage, so if you can see the files in both in the system picker it should work here.

 13·4 months ago
13·4 months agoI see
import_images.shandscikit_learn_data, whatever this plugs into probably has a decent amount of compute access & someone could rack up quite the bill

 2·4 months ago
2·4 months agoAvoid Sengled. I switched to Innr Zigbee bulbs for repeater functionality & they’re better than the Sengleds in every way (except price, like $25/bulb but it’s worth it)

 2·4 months ago
2·4 months agoIf you don’t want to buy a domain you can try a reverse DNS lookup, your ISP may already give you one. Mine was C-XX-XX-XX-XX.hsd1.pa.comcast.net and I could get a let’s encrypt certificate with that. I did end up buying a domain but it was good for personal use
Not the original question, but if you have just a normal “Nest Thermostat” (Not learning or E) it has matter support and you can add it over matter without paying $5

 21·5 months ago
21·5 months agoIn America I just use my buddy Carl. He’s also my doctor.

 51·6 months ago
51·6 months agoLocalTuya on HACS, it’s a bit of a pain to setup and requires you to make a tuya dev account (free) but as far as I can tell you can delete it after, it’s just to get the security keys to actually control the devices, and then issue them locally. My devices were much more responsive after doing so

 1·7 months ago
1·7 months agoGlad to hear it worked! I edited the comment in case anybody stumbles across it with the same issue

 65·7 months ago
65·7 months agoIt’s not “best practice”, but a compromised key is a compromised key whether that key is used to connect 1 or 100 computers to a server. No, I can’t shut off access to exactly one machine, I do not however have any difficulty in shutting off access to every machine and replacing it with a new key. Your system and my system are no different with a single compromised key.
If I had 100 computers that I had to change identity files on each time it was compromised, and my keys were being compromised often, I would see a benefit from using multiple different keys.
Quit acting like I’ve left the front door to my house open when the door is locked but my roommate and I share the same key.



…I just put a Zigbee contact sensor on my mailbox lid and called it a day…