Stupid sexy crack head
Ghostalmedia
I’m from space!
- 54 Posts
- 447 Comments

 16·16 days ago
16·16 days agoHave you and the other active mods considered adding a civility rule in the sidebar?

 2·24 days ago
2·24 days agohttps://www.apple.com/customer-letter/answers/
Quote below
Has Apple unlocked iPhones for law enforcement in the past?
No.
We regularly receive law enforcement requests for information about our customers and their Apple devices. In fact, we have a dedicated team that responds to these requests 24/7. We also provide guidelines on our website for law enforcement agencies so they know exactly what we are able to access and what legal authority we need to see before we can help them.
For devices running the iPhone operating systems prior to iOS 8 and under a lawful court order, we have extracted data from an iPhone.
We’ve built progressively stronger protections into our products with each new software release, including passcode-based data encryption, because cyberattacks have only become more frequent and more sophisticated. As a result of these stronger protections that require data encryption, we are no longer able to use the data extraction process on an iPhone running iOS 8 or later.
Hackers and cybercriminals are always looking for new ways to defeat our security, which is why we keep making it stronger.

 3·24 days ago
3·24 days agoThis is for non e2ee cloud data. If you turn e2ee cloud encryption on, only you can access your cloud data. A government or police agency can’t access it, but you’re also kind of fucked if you need Apple’s support to access backup. So maybe leave it off for old parents.

 4·24 days ago
4·24 days agoThat key is not for locally encrypted data, locked devices or e2ee data.
https://support.apple.com/en-gb/guide/security/sec973254c5f/web
If you turn this on, Apple can’t not decrypt anything you have stored in the cloud with that key.
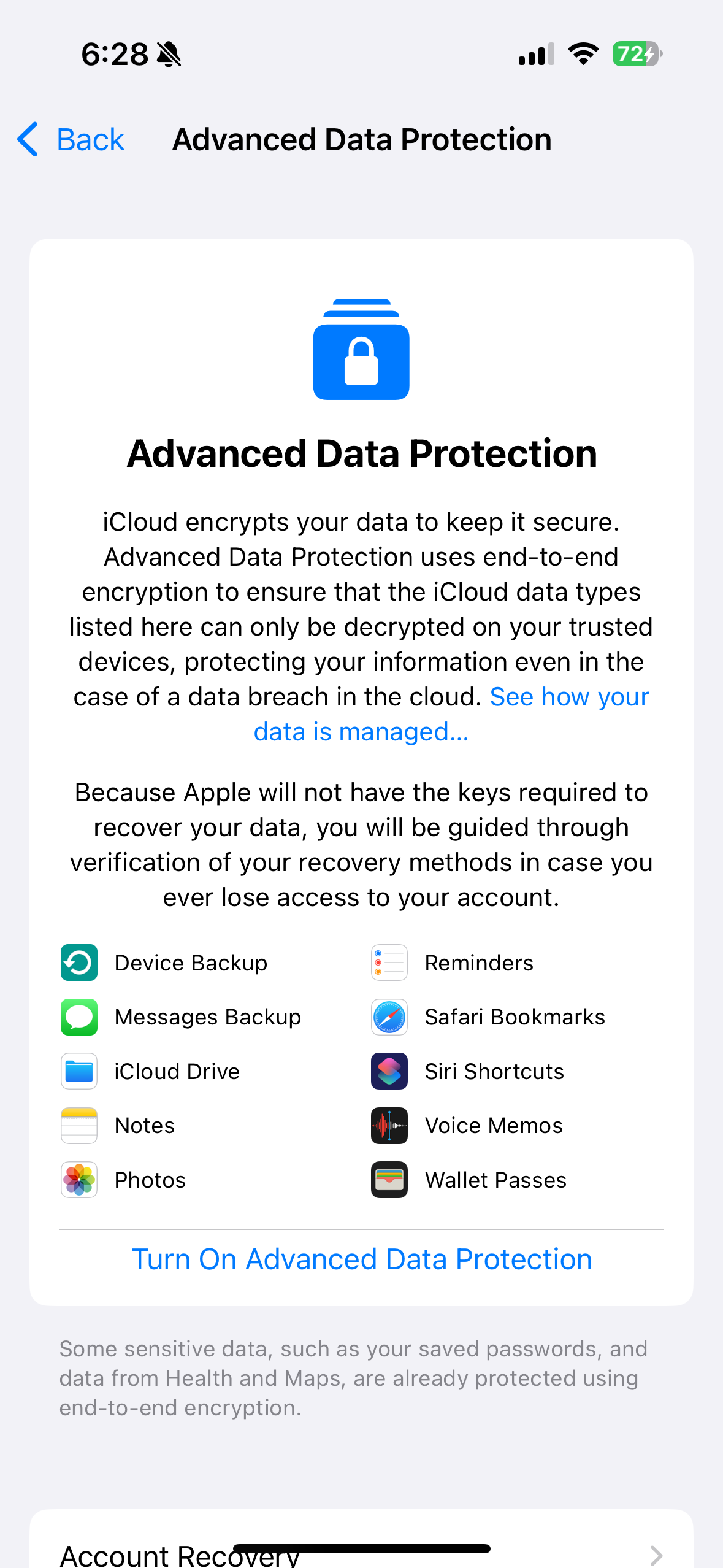

 5·25 days ago
5·25 days agoDo you have a source for that?
Because Apple has had a lot of very prominent court cases about unlocking phones for cops, and they famously haven’t done that. They, like other cloud service providers, have forked over cloud storage data, that isn’t e2ee, when given a warrant.

 71·25 days ago
71·25 days agoThey’ll hand over unencrypted cloud data, but they are not decrypting E2EE cloud data. They literally can’t. They don’t have the key. If they had a key, it would be a monumental security vulnerability.
This is why governments and cops have dragging them into courts for years.

 6·25 days ago
6·25 days agoScouting locations for surveillance pidgins and presidential weather control stations.

 12·26 days ago
12·26 days agoOnce you get 3/4 through this article, and get to the actual content, it’s pretty underwhelming. Apple was basically just showing cops that they could be querying their existing databases with iOS mobile and or CarPlay experiences.

 181·26 days ago
181·26 days agoAfter reading the article, it doesn’t look like any of this contradicts what they’re been selling. Encrypted data is still locked down. IMHO, this title is fairly clickbaity.
A lot of this looks like iOS / CarPlay versions of policing / public records database software that was previously on platforms like Windows.

 301·26 days ago
301·26 days agoThis title seems kind of clickbaity. Most of the native apps are for querying existing government and police databases. We’re talking about accessing records via CarPlay, as opposed to using a bulky Window’s laptop docked in a center console.
Apple is still not offering governments a backdoor into encrypted content.

 22·28 days ago
22·28 days agoThe E 686 Salad Sandwich was intel’s best CPU.
Prove me wrong.
pro wrestler

Real talk - lemmy’s mod tools blow, and the only way to combat this shit is if more people volunteer to help keep an eye on the report inbox.
So if you see a community that is struggling to address reports in a timely way, they’ll likely appreciate anyone that offers to help mod.

 21·1 month ago
21·1 month agoAs someone who works in data privacy, I don’t think the DS crazy ever died down. It’s bigger and more complex than ever. People just got tired of saying “big data” at Silicon Valley bars.

 12·1 month ago
12·1 month agoGen X and Boomers looking at Millennials… “I wish my knees and back were in that good of shape.”





https://www.urbandictionary.com/define.php?term=Hate sex