A Basil Plant
InfoSec Person | Alt-Account#2
- 3 Posts
- 22 Comments

 9·1 month ago
9·1 month agoJust purchased a server license (for life). Not only is this update jam packed full of nice features, but a lot of their updates are. I’ve been self-hosting it (on a VPS) for the past year and it’s about time I supported them
Also fuck off with this attitude man. I’m not attacking you, learn how to speak to people.
Sorry. I get quite triggered when people add pseudo-labels to distributions, mainly Debian being outdated. Looking back, I was quite harsh and I apologize.
However, you’re actively spreading the false narrative by saying Debian’s not good for “general computing” - this is what triggers me. A distribution is nothing but its package manager and some defaults. Some have different defaults and package managers.
Older packages can be difficult for new users who want a computer to “just work”.
The only place this makes a difference is with the latest hardware which OP does not have. I have more recent hardware than OP and Debian 13 + KDE Plasma 6 works out of the box.
It’s fine for general computing, but not great.
Again, I really hate this sentence. I will tone down the rudeness this time in explaining why. I have daily-driven Debian for years with AMD + Intel CPUs, Nvidia GPUs (1070, 3060) with use cases ranging wildly through the years. I cannot fathom what kind of general computing cannot work. If you say specialized computing, I would still disagree as there are always ways to make things work.
Just off the top of my head where things are iffy with Debian: bat cannot be installed via a package manager, but not on most distros anyway. There’s a deb package though which works. Similar with dust, although more distros have it in their package manager.
Debian, like you said, is rock-solid stable. In my many years of developing code, university courses, daily work (research), maintaining servers with wildly different usages, Debian’s “outdated” packages have only let me down once and that was with a LaTeX package which could be installed via ctan anyway.
Debian is rock-solid stable, but lacks newer packages. It’s great for a server, not so great for […] general computing.
What the fuck??? I’ve been daily driving Debian for years now on my personal laptops, desktop, mini PC, and mutliple servers. I’ve found and reported Linux kernel vulnerabilities on my trusty Debian systems.
What do you mean it’s not so great for general computing? What can’t you do with Debian computing-wise that you can do with other distros? The only issues I’ve ever had was with some LaTeX packages being older versions. You just get that from CTAN and install that manually.
This is such a ridiculous comment. What do you do on a server that’s not general computing? You’re doing a subset of general computing??? How does a fucking distro actively prevent you from doing general computing???

 5·2 months ago
5·2 months agoThank you for the comment!
Most of the beautiful hardwork was done by the store - I just pointed, zoomed, focused, and shot. It doesn’t feel like I did much to the already existing grandeur.
Installed it on my desktop and the process was painful (my fault) because I ran out of space on my boot ssd (128Gigs) while doing the upgrades.
I don’t really have much on my boot ssd and all my important data is on my laptop, backed up to my servers, or on my desktop’s HDD. I did a fresh install with a kde live usb stick and that went smooth, until something with the nvidia drivers prevented the display server from launching.
Thankfully, I’ve been through this charade multiple times in the past, and I’m significantly more experienced in dealing with the kernel these days. Adding the nvidia-drm modeset kernel command line launch param worked, and my system is running deb 13. I’m so happy I have KDE plasma 6.
Overall, a one hour process. Could have been faster if I had free space on my system lol. I’m a bit more reluctant to upgrade my servers at the moment, but I may in the upcoming months.
One minor thing: they updated their apt sources (https://repolib.readthedocs.io/en/latest/deb822-format.html, https://unix.stackexchange.com/questions/498021/deb822-style-etc-apt-sources-list#583015). Idk why, but the installer didn’t create & populate the .sources file. After a quick check of the man page, I created the file and it worked.
Oh boy, this was a 20 minute rabbit hole.
Tl;Dr: this is probably AI generated.
Using google image search, I found is that it was created by this account in Oct/2024:
https://www.instagram.com/gothtoon/p/DBh-p4WgThS/
Alternative front-end: https://imginn.com/p/DBh-p4WgThS/
There is the copyright symbol with this user in this image.
If you go through the comments and other posts by that user, it does look AI generated. Their threads account has a linktree, which has a link to a discord server, which I momentarily joined to see what the deal is about.
Looks like it’s a project started by a user named Emo Bot 9000, and they’ve created a bunch of characters, the most famous of which is the frog mage. This is a message on discord that supports this:
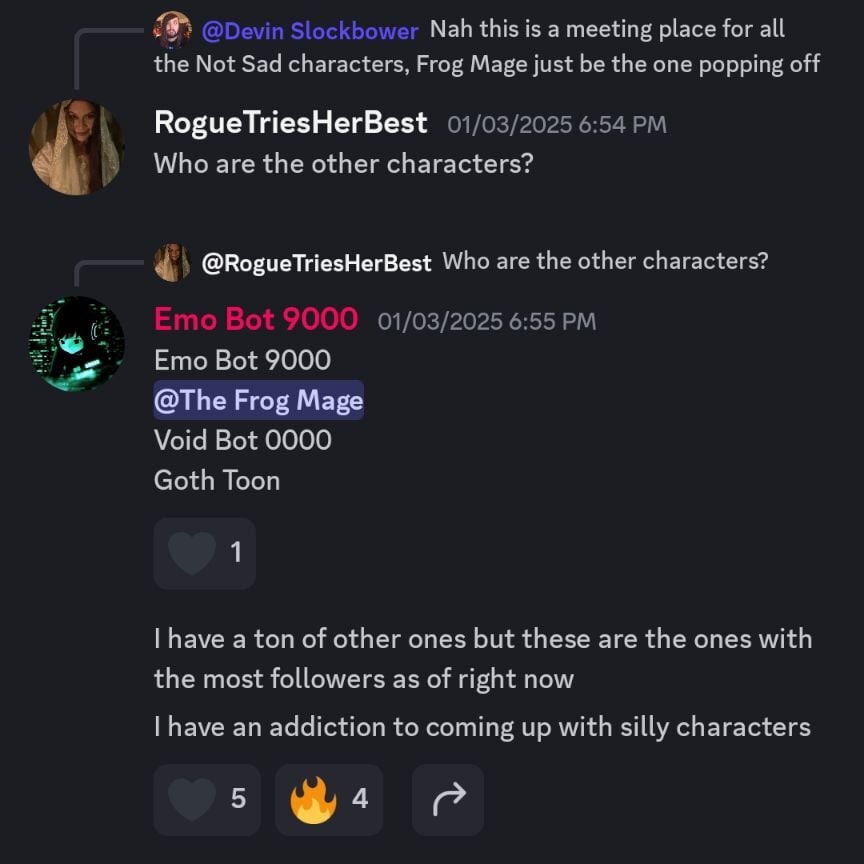
Another user asks whether the frog mage stuff is made using AI, and Emo Bot 9000 essentially replies yes:
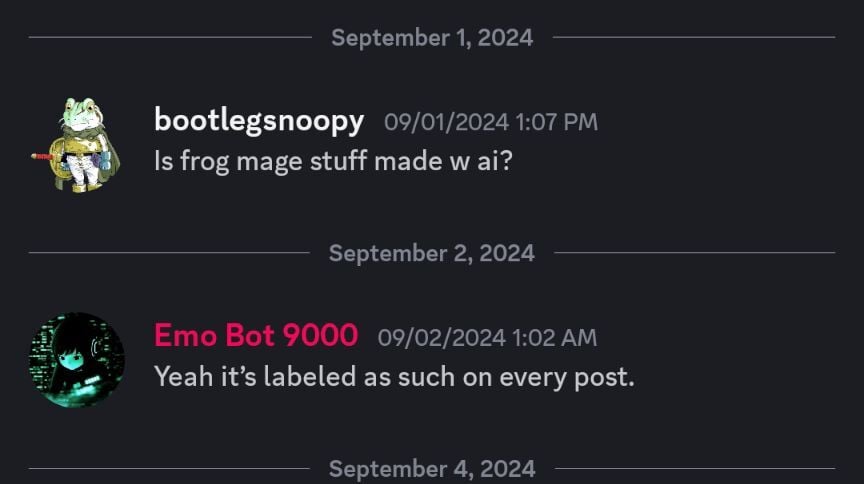
Now, although the image in this lemmy post is, to the best of my searching, nowhere explicitly labeled AI, I think it mostly points to being generated by AI. The simplest way to confirm would be to ask them on their discord directly, which I don’t intend to do.
Although reverse search tells me there are earlier appearances of this image, they’re either false or the PFP of a commenter.

 3·1 year ago
3·1 year agoHuh, I hadn’t heard about this idea and a quick search on DDG returned this link: https://www.weforum.org/stories/2022/08/sustainable-data-centre-heating/
Interesting!
Yep! Series 4 hasn’t “released” on YouTube yet. I saw Paul William’s story on instagram that they’re releasing Series 5 on TV, but sadly I don’t have access to that. I’m fine being behind by 1-2 years though.
I’m a huge fan of the original British TM, but TM New Zealand is honestly amazing. The whole thing is available on YouTube (thanks Little Alex Horne + team!!!).
In my and many of my friends’ opinion, TM New Zealand Series 2 is one of the best TM series. TM New Zealand in general is absolutely unhinged.
Series 1 feels a bit off, which is probably because it’s unlike British TM. I got used to it fairly quick though.
TM NZ Series 3 (final episode releases on YouTube in 2-3 days)
Are you in Europe? This is a thing I’ve seen in Europe, but not in other countries.
I knew about the “Thour” meme, but still didn’t get why the directory turned compressed. My guess is that by licking the lemon, the directory folds in on itself, thus becoming compressed.
The debug version you compile doesn’t affect the code; it just stores more information about symbols. The whole shtick about the debugger replacing instructions with INT3 still happens.
You can validate that the code isn’t affected yourself by running objdump on two binaries, one compiled with debug symbols and one without. Otherwise if you’re lazy (like me 😄):
https://stackoverflow.com/a/8676610
And for completeness: https://gcc.gnu.org/onlinedocs/gcc-14.1.0/gcc/Debugging-Options.html
Excellent question!
Before replacing the instruction with INT 3, the debugger keeps a note of what instruction was at that point in the code. When the CPU encounters INT 3, it hands control to the debugger.
When the debugging operations are done, the debugger replaces the INT 3 with the original instruction and makes the instruction pointer go back one step, thereby ensuring that the original instruction is executed.
https://en.wikipedia.org/wiki/INT_(x86_instruction) (scroll down to INT3)
https://stackoverflow.com/a/61946177
The TL;DR is that it’s used by debuggers to set a breakpoint in code.
For example, if you’re familiar with gdb, one of the simplest ways to make code stop executing at a particular point in the code is to add a breakpoint there.
Gdb replaces the instruction at the breakpoint with 0xCC, which happens to be the opcode for INT 3 — generate interrupt 3. When the CPU encounters the instruction, it generates interrupt 3, following which the kernel’s interrupt handler sends a signal (SIGTRAP) to the debugger. Thus, the debugger will know it’s meant to start a debugging loop there.

 213·2 years ago
213·2 years ago… I am 100% certain that if they switched to being individually wrapped tomorrow, a complaint about excessive packaging would be one of the top posts here.
You’re undeniably right. The best situation would be to not have any wrapping at all… but with the crumb situation, that’d be another top post here :/





Is this image AI? the reflections in the window, the perfect snowman, that film grain filter… it looks too perfect to me.